If you are receiving too much spam, consider switching to Queensland Tech!
Email protocols were designed in 1970s, and was kind of based on the physical mailing system. The problem with this is that any mails can be delivered to you, and they can easily pretend to be from someone they are not. Today, we have a number of bolt-on systems that attempt to fix this.
How email is delivered
When you hit the send button, a copy of your email sent to your local email provider. eg. If your using gmail, it will be sent to a Google server, if your using hotmail, it will go to a Microsoft server. This is because your email address is actually sitting on their server (called a mailbox), and not at your device, your device is just sync’ing with your email provider. Once they have a copy, the email provider will then look for the domain name its being sent to, this is the part after the [at] sign, and will attempt to communicate with receiver’s email server; once connected it will send a copy of your email over to their server. Their server will then look for the user, the bit before the [at] sign, and store that copy of the email within their inbox. When their email device next sync’s with their locate email provider, they will get notified of an email being delivered.
Email Scraping
There are a number bots which are constantly searching through thousands of web pages looking for any email addresses which have been published. When one is found, its added to their database of people of which they will send spam emails to. So its recommend not to publish your email address on web page, at least in a format that a bot can read. There are a couple of different techniques that stops a bot from being able to read your email address; the most common method is to not display it as text, but as an image. It’s a lot more difficult for a bot to read text that is inside an image, so generally they don’t go processing every image looking for an email addresses, but this may change in the future. Email addresses can also be hidden from a bot using a clever bit of software; the server can obfuscate the email address and transmit it along with another (JavaScript) software that will decrypt it only for a real user; it works so seamlessly, that you won’t notice any difference.
When email isn’t delivered
There are a number of things that can go wrong when sending an email, but the most common problem today is that the email address being used hasn’t been typed correctly! When you send an email, your device will need a working internet connection as to pass a copy of the email to your email provider. The email provider will then attempt to find the correct server to deliver the email to, and sometimes receiving email server may have a problem or may not even exist. When this happens, you would normally receive a reply from your own email provider saying it was unable to deliver your email.
Some email providers blacklist other email providers. Sometimes when your email is attempting to be delivered, the receiving provider may have decided not to respond or they may accept the email but then deliver it to the user’s spam folder. This often happens if the source email provider has been put on a blacklist; or it can happen if the email content contains too many website links; or has file attachments it deems to be dangerous to the user.
Spam/Junk folders
Most email systems now have a spam or junk folder, and any emails that appear to be spam/junk will get put in to this folder instead of your inbox. The rules that determine which emails go where is widely varied, but its usually the email provider that does a spam scoring testing, and will deliver the email to the spam box if the score is over specific threshold. Most providers use 3rd party services for this scoring process, normally performed by the server that is accepting the email. Some email devices will also perform their own spam check, and will move emails from the inbox to the spam box. For example, many email apps allow you to specify if a email is spam, it will then put any future emails from the same source in to the spam box.
Blacklists and Whitelists
Blacklist: Many email system include the ability to blacklist an email address, eg. within Outlook, you can right click on an email, and select ‘Junk’, which will tell your email system to put that email address in your personal blacklist. Some systems will also send a notification back as to tell the server that you have categorised it as junk mail; the server, after receiving a number of notifications will add it to its own global blacklist so that these emails don’t get delivered to other users inbox either.Whitelist: Email systems usually include a place you can list your contacts that you often email, however this same list is often treated as a whitelist, ie. any emails being delivered that match one of your contacts would normally get delivered to your inbox. Some corporate email systems also have a global whitelist as make sure their business partners emails are not blocked.
These Blacklist and Whitelist are applied to the email address, but can also be applied to the mail server IP address which is sending the email. If an email server is sending lots of different emails that score highly as spam, they will soon get the whole mail server blacklisted.
What is Spoofing
Spoofing means to pretend to be another identity, and with email it is fairly easy to do. With a small amount of technical knowledge, anyone can send email on your behalf, but its done without accessing your email. Its just like putting a letter in the post-box, but the return mail address written on the back not being yours. So, when these email are returned, it will return to you. Sometimes a hacker may spoof without even using your email address, but just your name, as some modern email systems will show the name a lot more clearly then showing you the actual source email address. This can sometime catch people off-guard, especially if the email content looks similar to what they were expecting.
What is Phishing
Phishing uses spoofing as to deliberately try to trick you and make you click on a link within the email. eg. an email pretending to come from PayPal asking you to ‘click here’ to reset your account password. For phishing to work, they would also need to create a pretend website, one that looks exactly like what your expecting, but if you look carefully at the URL address, its not the website you think it is, it just looks the same. So when you click on that email that says reset your password and you are then presented with a page that says enter your current password and a new password, you maybe tricked in to typing your password in. These websites won’t let you login, they cant, they exist just to capture the password you entered and send this to the hacker. The hacker will then go to the real website, and use the password you gave to login to your account.
Phishing is now the most common tool that a hacker uses. Its become increasingly difficult to find vulnerabilities within computer systems, its much easier today to trick the user in to giving up their password!
How to stop spoofing & phishing
Most email system now include a number of extra technologies to help determine what emails have been authorised to be sent and which are fake. Most of these technologies make use of the DNS, the domain name system. Use this button to find out how to report phishing attacks:
Report Phishing
SPF – Sender Policy Framework
An SPF record is a DNS txt record which specifies the IP addresses of email servers which are authorised to send email on behalf the domain.
A receiving email system can now check the SPF of the domain against the IP address of the server that sent the email. If they don’t match, then it was sent from an unauthorised email server and would normally be placed in the spam/junk folder.
An SPF record is appended to the DNS as a TXT record on the root host address, here’s an example with explanation:
v=spf1 ip4:157.55.9.128/25 ip6: ip6:0:0:0:0:0:ffff:cc4f:c5d4 a mx include:spf.protection.outlook.com ptr:microsoft.com ~all
- v=spf1 – The first bit must always be there as to acknowledge that we are now looking at an spf record.
The next parts will list which servers are allowed, (and can also list servers not allow) - ip4:157.55.9.128/25 – accepted server email address range
- ip6:0:0:0:0:0:ffff:cc4f:c5d4
- a – accept email from the website server
- mx – accept email from coming from the same place we receive email
- include:spf.protection.outlook.com – also include the spf records found at this address
- ptr:microsoft.com – include server which has this domain name
- ~all The very end, is flag that basically says what to do if none of the expected servers was listed. -all means strictly ignore all other servers. ~all means, probably should ignore other servers.
DKIM – Domain Keys Identified Mail
DKIM uses key pairs as to digitally signed emails. It publishes the public key as an additional domain DNS txt record under the subdomain ‘default._domainkey’, and will put the signature key within the headers of every email that is sent from the domain. When the email is received, the email server can read the signature and compare it to the domain key as determine if the domain authorises the email. Here’s example of what DKIM puts within the DNS:
v=DKIM1; k=rsa; p=MIIBIjANBgkqhkizG9w0BAQEFAAOCAQ8AMIzIBCgKCAQEzA3QI AXhjpriqQOJmq2k1z3B7Zqd
- v=DKIM1 – The first bit must always be there as to acknowledge that we are now looking at a DKIM (version 1) record.
- k=rsa – type of certificate being used
- p=MIIB.. – public key
Note, this might be a problem if you send email from multiple sources.
DKIM Checker
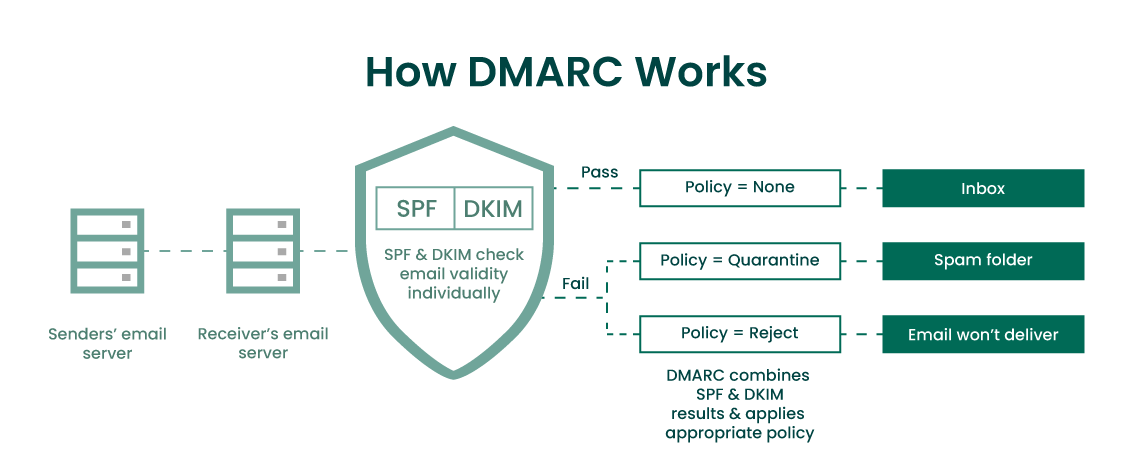
DMARC – Domain-based Message Authentication, Reporting, and Conformance
This is an additional DNS txt record published using the subdomain ‘_dmarc’. The information tells the email receiver what actions it should take when either the SPF and/or DKIM fails. You can also specify an email address for the server to send reports of any emails it had received from you that wasn’t authorised. Here’s an example:
v=DMARC1; p=quarantine; adkim=s; aspf=s; rua=mailto:example@example.com
- v=DMARC1 – The first bit must always be there as to acknowledge that we are now looking at a DMARC (version 1) record.
- p=quarantine – The action to perform when failing the test, either quarantine, reject or none
- adkim=s – Either s or r, standing for Strict or Relaxed. Relating to DKIM actions.
- aspf=s – Either s or r, standing for Strict or Relaxed. Relating to SPF actions.
- rua=mailto:example@example.com – Email address to send aggregate reports to
- ruf=mailto:example@example.com – Email address to send forensic reports to
 DMARC Generator DMARC Report Analyzer
DMARC Generator DMARC Report Analyzer
Further info
If you are receiving too much spam, consider switching to Queensland Tech. Our spam filters work exceptionally well, as we use all of the above technologies to decide whether the email being sent you should go in your inbox or your spam/junk folder. All this is done automatically with the exception of DMARC which you would need to set your policy you prefer.
Mailboxes are also virus scanned too, but this is a separate topic.
We can setup any type of email address for you. Learn more about our email packages.



 ABN: 58 196 482 040
ABN: 58 196 482 040
NDIS SEO services in Queensland can help you achieve just that! We’re committed to providing the most affordable SEO solutions tailored to your needs. Contact us now to start improving your website’s visibility and reach more clients!
It seems that the information you provided isn’t directly related to a specific service on our website. However, I can help you with SEO services tailored to your needs. If you have specific questions or requirements, feel free to ask, and I’ll be happy to assist you further.